Solved[December 2023] BCS41 - Fundamental of Comptuer Networks | IV SEM BCA IGNOU
Hey there! Welcome to KnowledgeKnot! Don't forget to share this with your friends and revisit often. Your support motivates us to create more content in the future. Thanks for being awesome!
1. (a) What is MD5 Digest? Explain the steps for the process of generating 128-bit MD5 digest from any given number and key. (10 marks)
Answer:
MD5 (Message-Digest Algorithm 5) is a widely used cryptographic hash function that converts an arbitrary-length input into a fixed 128-bit hash value, commonly referred to as the MD5 digest. This digest is typically used to verify data integrity, ensuring that the data has not been altered or tampered with. The process of generating an MD5 digest involves the following steps:
→ Step 1: Padding - The original message is padded with a single '1' bit followed by '0' bits until the length of the message (in bits) is congruent to 448 modulo 512. This step ensures that the message length is just 64 bits short of being a multiple of 512.
→ Step 2: Append Length - After padding, a 64-bit representation of the original message length (before padding) is appended to the end of the padded message. This 64-bit number is added as a little-endian integer, making the final message length a multiple of 512 bits.
→ Step 3: Initialize MD Buffer - Four 32-bit variables, A, B, C, and D, are initialized to specific constants. These variables are used to store intermediate and final results of the hash function.
→ Step 4: Process Message in 512-bit Chunks - The padded message is divided into 512-bit chunks. Each chunk is processed in four rounds, with 16 operations per round, using bitwise operations and modular addition to mix the bits.
→ Step 5: Produce Output - The values in A, B, C, and D after processing all the chunks are concatenated to produce the final 128-bit hash value. This value is the MD5 digest, typically represented as a 32-character hexadecimal number.
MD5_hash=MD5(message).
1. (b) How is sampling done from analog signals? Explain through an illustration. (7 marks)
Answer:
Sampling is the process of converting an analog signal into a digital signal by taking periodic measurements of the analog signal's amplitude. The essential steps for sampling an analog signal are:
→ Step 1: Select Sampling Rate - Choose a sampling rate that is at least twice the highest frequency in the analog signal. This is known as the Nyquist rate and is crucial to avoid aliasing, where higher frequency components are indistinguishable from lower ones.
→ Step 2: Measure Signal - At each sampling instant, measure the amplitude of the analog signal. These sampling points are typically taken at regular intervals.
→ Step 3: Quantization - Convert these amplitude measurements into a finite set of values, which are then represented in digital form. This step involves approximating the amplitude of the signal to the nearest value in the set, leading to a digital representation of the signal.
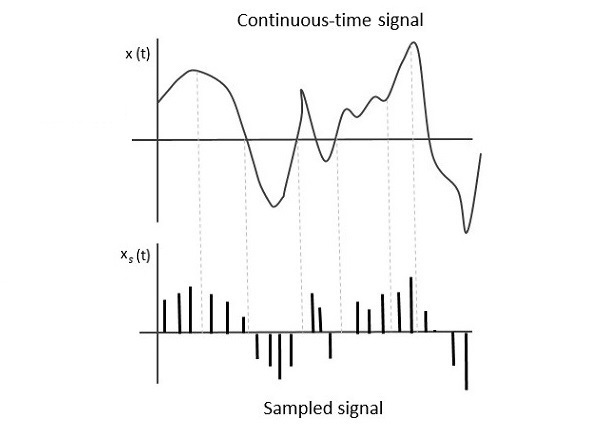
For example, if a 1 kHz sine wave is sampled at a rate of 8 kHz, each sample would capture a snapshot of the sine wave’s amplitude at that particular moment, ensuring accurate reconstruction of the original signal.
1. (c) Given data frame as 1101011011 and generator polynomial G(x) = x4 + x + 1, derive the transmitted frame using CRC method. Write all the steps involved in the process. (10 marks)
Answer:
To derive the transmitted frame using the CRC (Cyclic Redundancy Check) method for the data frame 1101011011 with the generator polynomial G(x)=x4+x+1, follow these steps:
→ Step 1: Append Zeros - Append four zeros (equal to the degree of the generator polynomial) to the data frame, resulting in 11010110110000.
→ Step 2: Polynomial Division - Perform modulo-2 division of the extended data frame by the generator polynomial (10011). This is done by aligning the leftmost bit of the polynomial with the leftmost bit of the dividend and performing XOR operations.
→ Step 3: Calculate Remainder - After the division, the remainder is calculated. For our data, the remainder is 0110.
→ Step 4: Append CRC - Append the remainder to the original data frame, which gives us 11010110110110.
The transmitted frame, therefore, is 11010110110110. This frame, when received, can be checked against the generator polynomial to verify data integrity.
1. (d) How many networks can each IP address class A, B, and C have? Also find the number of hosts per network in each of the given address class. (6 marks)
Answer:
IP address classes A, B, and C have different capacities for networks and hosts per network:
→ Class A: Provides for 128 networks (from 1.0.0.0 to 126.0.0.0) with up to 224−2 (16,777,214) hosts per network. The large number of hosts is due to the use of 24 bits for host addresses.
→ Class B: Offers 16,384 networks (from 128.0.0.0 to 191.255.0.0) with up to 216−2 (65,534) hosts per network. This class uses 16 bits for network addresses and 16 bits for hosts.
→ Class C: Supports 2,097,152 networks (from 192.0.0.0 to 223.255.255.0) with up to 28−2 (254) hosts per network. Here, 24 bits are used for network addresses, and only 8 bits are left for host addresses.
1. (e) Discuss the working of ARP and RARP. Also, differentiate between the two. (7 marks)
Answer:
ARP (Address Resolution Protocol) is used to map an IP address to a physical MAC address in a local network. When a device wants to communicate with another device, it sends an ARP request to the network to find the MAC address associated with a specific IP address. The device with the matching IP address replies with its MAC address, enabling communication.
RARP (Reverse Address Resolution Protocol) allows a device to obtain its IP address from a known MAC address. This is particularly useful for diskless workstations that need to discover their IP address at boot time to establish network communication.
Differences:
→ Purpose: ARP is used for translating IP addresses to MAC addresses, while RARP is used for discovering IP addresses from MAC addresses.
→ Usage: ARP is widely used in general network communication to facilitate data transfer between devices, whereas RARP is mainly used in network initialization scenarios, such as booting diskless workstations.
2. (a) Discuss the following in the context of network management: (6 marks)- (i) Configuration management
- (ii) Accounting management
Answer:
(i) Configuration Management:
Configuration management involves the systematic handling of network and system configurations to ensure the integrity, reliability, and performance of network operations. It includes several key aspects:
Inventory Management: Keeping an accurate and updated record of all network devices and their configurations to facilitate management and troubleshooting.
Change Management: Implementing a structured process to manage changes in network configurations, minimizing risks and disruptions. This includes planning, approving, and documenting changes to prevent accidental conflicts and ensure all changes are reversible.
Compliance: Ensuring that network configurations adhere to organizational policies, industry standards, and regulatory requirements. Regular audits and checks are performed to maintain compliance.
Backup and Restore: Regularly backing up configurations to prevent data loss and enabling quick restoration in case of configuration failures. Automated tools can be used to perform scheduled backups and facilitate rapid recovery.
(ii) Accounting Management:
Accounting management focuses on tracking and managing the usage of network resources to facilitate billing, capacity planning, and cost management. Key functions include:
Usage Monitoring: Continuously monitoring the usage of network resources by users, applications, or departments to ensure fair and efficient distribution. This includes tracking bandwidth, data transfer, and resource consumption.
Billing: Generating detailed reports and invoices for resource usage, particularly important for service providers and organizations that charge for network services. This helps in cost recovery and resource allocation.
Quota Management: Setting and enforcing quotas to prevent excessive usage and ensure that resources are available for all users. Quotas can be based on data usage, bandwidth consumption, or time.
Trend Analysis: Analyzing usage data to identify trends, forecast future demand, and make informed decisions about resource allocation and capacity planning. This helps in optimizing network performance and planning for infrastructure upgrades.
2. (b) What are the important features of an ATM switch? (4 marks)
Answer:
An ATM (Asynchronous Transfer Mode) switch is a high-speed networking device designed to handle ATM cells efficiently. Important features include:
High Throughput: Capable of supporting high data transfer rates, making ATM switches suitable for demanding broadband applications. This ensures that large volumes of data can be transferred quickly.
Low Latency: Ensures minimal delay in data transmission, which is crucial for real-time applications like voice and video communication where timely delivery is essential for quality of service.
Cell Switching: Utilizes fixed-size cells (53 bytes) for data transfer, which simplifies traffic management and enables predictable performance. This uniform cell size allows for efficient and consistent handling of data packets.
Quality of Service (QoS): Provides mechanisms to prioritize different types of traffic, ensuring reliable and timely delivery based on predefined service levels. QoS features allow for the allocation of bandwidth to critical applications, maintaining performance under varying network conditions.
2. (c) What are the two categories of ICMP messages? Give two examples of each. (6 marks)
Answer:
ICMP (Internet Control Message Protocol) messages are classified into two main categories: error messages and informational messages.
Error Messages:
1. Destination Unreachable: Indicates that a packet could not reach its intended destination, due to reasons like network failure, no route to the destination, or the destination being administratively prohibited.
2. Time Exceeded: Signals that a packet's time-to-live (TTL) has expired. This is commonly used in the traceroute utility to trace the path packets take to a destination, helping diagnose routing issues.
Informational Messages:
1. Echo Request: Used by the ping command to test connectivity by sending a request for a response from a remote host. It checks whether the host is reachable and measures round-trip time.
2. Echo Reply: The response to an echo request, indicating that the remote host is reachable and operational. This message confirms the reception and processing of the echo request.
2. (d) Differentiate between Virtual Circuit and Datagram. (4 marks)
Answer:
Virtual Circuit:
A virtual circuit provides a pre-established, dedicated path for data transmission, ensuring a consistent route for the duration of the communication session. It involves setting up a connection before data transfer begins, much like a telephone call where the connection remains consistent throughout the session.
Ordered Delivery: Virtual circuits ensure that data packets are delivered in the same order they were sent, maintaining data integrity and sequence.
Fixed Path: The data follows a predetermined path, providing predictable performance and simplifying troubleshooting.
Examples: Frame Relay and ATM networks, where virtual circuits are established before data transfer begins.
Datagram:
A datagram is a self-contained, independent packet that contains all the information needed for routing from the source to the destination, without relying on established paths. Each packet is routed independently, much like mailing letters where each letter can take a different route to its destination.
Unordered Delivery: Delivery order is not guaranteed, and each packet may arrive at the destination in any order.
Dynamic Path: Each packet can take a different path based on current network conditions, providing flexibility and resilience.
Examples: Commonly used in IP networks like the Internet, where each packet is routed independently.
3. (a) Explain the following features of IPv6: (5 marks)- (i) Tunneling
- (ii) Dual IP Stack
Answer:
(i) Tunneling:
Tunneling is a technique used to encapsulate IPv6 packets within IPv4 packets to facilitate their transmission over an existing IPv4 network. This method enables the coexistence of IPv6 and IPv4 networks during the transition period by allowing IPv6 traffic to pass through IPv4 infrastructure without requiring immediate, widespread changes to the existing network setup.
Types of Tunneling: Various tunneling methods include 6to4, Teredo, and ISATAP, each with specific use cases and configurations to ensure smooth IPv6 packet transmission over IPv4 networks.
Advantages: Simplifies the transition to IPv6, maintains compatibility with IPv4, and allows for gradual network upgrades.
(ii) Dual IP Stack:
Dual IP stack refers to the implementation of both IPv4 and IPv6 protocols on a single device or network infrastructure. This allows devices to handle both IPv4 and IPv6 traffic, ensuring compatibility with both types of networks. Dual stack implementation is crucial for a smooth transition from IPv4 to IPv6, as it enables devices to communicate using either protocol based on the destination address.
Implementation: Devices running dual stack can simultaneously operate IPv4 and IPv6, choosing the appropriate protocol based on the destination IP address.
Advantages: Provides flexibility, ensures backward compatibility, and facilitates a seamless transition from IPv4 to IPv6 without disrupting existing services.
3. (b) What is the problem with PSK? Explain how it may be solved. (5 marks)
Answer:
PSK (Phase Shift Keying) is a digital modulation technique that encodes data by varying the phase of a carrier signal. The main issue with PSK is its susceptibility to noise and phase shifts, which can cause data errors, particularly in higher-order PSK schemes where more phase states are used.
Noise Sensitivity: PSK's performance degrades in the presence of noise, as phase shifts can be easily distorted, leading to errors in data interpretation.
Phase Ambiguity: Small errors in phase detection can result in incorrect data decoding, especially in higher-order PSK where phase states are closer together.
Solutions:
Differential Encoding: This method encodes data as changes between successive phase states rather than using absolute phases. This helps to mitigate errors caused by phase shifts. By using differential phase shifts, the receiver can decode the data based on the relative changes, reducing the impact of phase ambiguity.
Error-Correcting Codes: Adding redundancy to the transmitted data allows the receiver to detect and correct errors caused by noise and phase shifts. Techniques such as forward error correction (FEC) can significantly enhance the reliability of data transmission.
More Robust Modulation Schemes: Using modulation schemes like QAM (Quadrature Amplitude Modulation) that combine amplitude and phase variations can improve reliability and performance in noisy environments. QAM provides a better signal-to-noise ratio and more efficient use of bandwidth compared to PSK.
3. (c) What is TCP’s sliding window? Explain Silly Window Syndrome with the help of a diagram. (10 marks)
Answer:
TCP’s sliding window is a flow control mechanism that regulates the amount of data a sender can transmit before requiring an acknowledgment from the receiver. It ensures efficient use of network resources and prevents congestion by dynamically adjusting the window size based on network conditions.
The sliding window mechanism works as follows:
Window Size: The sender can send multiple packets up to the window size before needing an acknowledgment from the receiver.
Acknowledgments: The receiver acknowledges the receipt of data packets, allowing the sender to slide the window forward and send more data.
Dynamic Adjustment: The window size can be adjusted based on network conditions, receiver's buffer capacity, and the rate of acknowledgments, ensuring optimal data flow.
Silly Window Syndrome (SWS) occurs when small segments of data are sent and acknowledged frequently, leading to inefficient use of bandwidth and increased overhead. SWS typically arises when the receiving application reads data in small chunks, causing the window size to repeatedly reduce to a small value.
The following diagram illustrates Silly Window Syndrome:
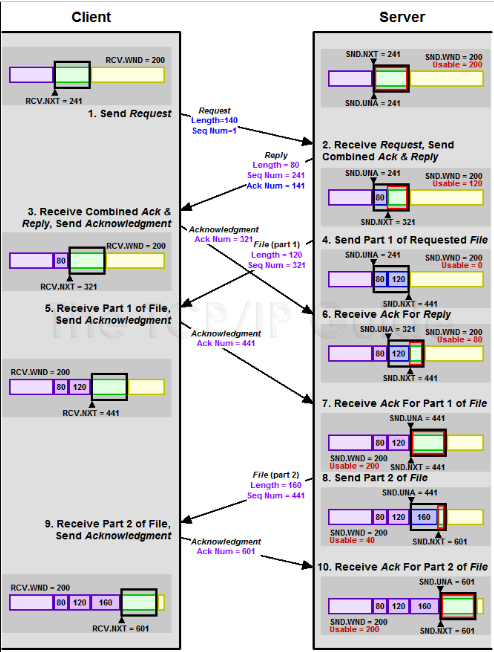
Explanation:
1. The sender transmits a small segment of data because the window size is small.
2. The receiver acknowledges the small segment and advertises a small window, due to its small buffer availability.
3. The sender continues to send small segments, resulting in inefficient data transfer and increased overhead.
To mitigate Silly Window Syndrome, several strategies can be employed:
Nagle's Algorithm: Combines small packets into a single larger packet before sending, reducing the number of small packets on the network.
Clark's Solution: Prevents the receiver from advertising a small window size until it can accommodate a larger segment, ensuring more efficient data transfer.
Delayed Acknowledgment: The receiver delays sending an acknowledgment until it can combine multiple small segments into a larger acknowledgment, reducing the frequency of small window advertisements.
4. (a) Explain Time Division Multiplexing (TDM). Discuss the advantages and disadvantages of TDM. Also, give applications of TDM. (10 marks)
Answer:
Time Division Multiplexing (TDM):
Time Division Multiplexing is a method of transmitting multiple signals over a single communication channel by dividing the time frame into several time slots. Each signal is assigned a specific time slot in which it can transmit its data, effectively sharing the channel among multiple signals.
Advantages of TDM:
Efficient Use of Bandwidth: TDM allows multiple signals to share the same transmission medium, maximizing the use of available bandwidth.
Simple Implementation: The concept of dividing time slots is straightforward and can be easily implemented in digital communication systems.
Synchronization: TDM systems use precise timing, which helps in maintaining synchronization between the transmitter and receiver.
Flexibility: TDM can accommodate different types of data streams, such as voice, video, and data, by allocating appropriate time slots.
Disadvantages of TDM:
Latency: The time division nature of TDM can introduce latency, especially if there are many signals sharing the same channel.
Synchronization Requirement: Precise timing is essential to ensure that data is transmitted and received correctly, requiring complex synchronization mechanisms.
Limited Bandwidth Allocation: Each signal gets a fixed time slot, which might lead to inefficient use of bandwidth if some signals have lower data rates than others.
Applications of TDM:
Telecommunications: TDM is widely used in digital telephony systems to combine multiple phone calls over a single transmission line.
Data Communications: In networking, TDM is used in leased line services and digital subscriber lines (DSL) to transmit multiple data streams.
Satellite Communication: TDM is used to transmit multiple data streams from earth stations to satellites and vice versa.
4. (b) What is the Three-way handshaking method? Draw and explain the connection establishment and termination in TCP using the Three-way handshaking method. (10 marks)
Answer:
The Three-way handshake is a method used in TCP/IP networks to establish and terminate a reliable connection between a client and server. It involves three steps to ensure that both parties are ready to transmit and receive data.
Connection Establishment:
SYN: The client sends a SYN (synchronize) packet to the server, indicating its desire to establish a connection.
SYN-ACK: The server responds with a SYN-ACK (synchronize-acknowledge) packet, acknowledging the client's request and indicating its readiness to establish a connection.
ACK: The client sends an ACK (acknowledge) packet back to the server, confirming the connection establishment. Data transfer can now begin.
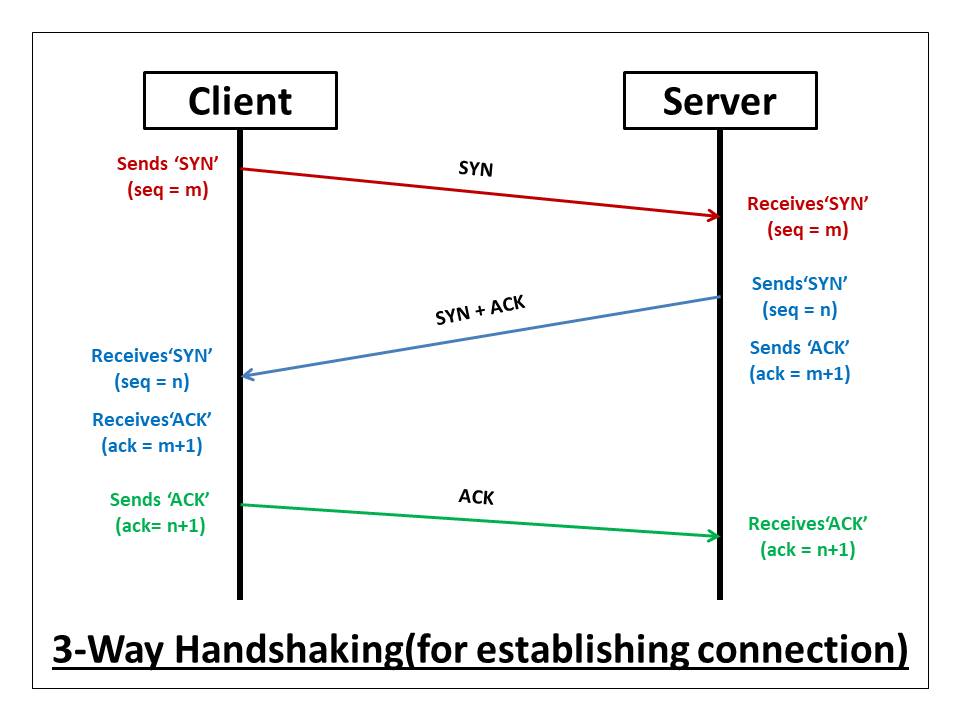
Connection Termination:
FIN: The client sends a FIN (finish) packet to the server, indicating its desire to terminate the connection.
ACK: The server acknowledges the client's FIN packet with an ACK, indicating that it is ready to close the connection.
FIN: The server then sends its own FIN packet to the client, indicating its intent to close the connection.
ACK: The client acknowledges the server's FIN packet with an ACK, completing the termination process. The connection is now closed.

5. (a) Differentiate between the following: (10 marks)- (i) Circuit switching and Packet switching
- (ii) IPv4 and IPv6
Answer:
(i) Circuit Switching and Packet Switching:
Circuit Switching:
Circuit switching involves establishing a dedicated communication path between two endpoints for the duration of the connection. This method is commonly used in traditional telephone networks.
Dedicated Path: A single, dedicated path is established and maintained for the entire communication session.
Resource Reservation: Resources along the path are reserved for the duration of the connection, ensuring consistent quality.
Examples: Traditional telephone systems, ISDN.
Packet Switching:
Packet switching divides data into packets that are transmitted independently over the network. Each packet may take a different path to reach the destination.
Dynamic Path: Data packets can take multiple paths based on network conditions, leading to efficient use of network resources.
No Reservation: Resources are not reserved; packets are sent as and when resources are available.
Examples: Internet, Ethernet.
(ii) IPv4 and IPv6:
IPv4:
IPv4 is the fourth version of the Internet Protocol, using 32-bit addresses, allowing for approximately 4.3 billion unique addresses.
Address Format: IPv4 addresses are written in decimal format as four octets separated by periods (e.g., 192.168.1.1).
Header Complexity: IPv4 has a simpler header with fewer fields.
Examples: Widely used in home and enterprise networks.
IPv6:
IPv6 is the sixth version of the Internet Protocol, using 128-bit addresses, allowing for a vastly larger number of unique addresses.
Address Format: IPv6 addresses are written in hexadecimal format as eight groups of four hexadecimal digits separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
Header Complexity: IPv6 has a more complex header with additional fields to support advanced features.
Examples: Designed to replace IPv4, increasingly adopted in modern networks.
5. (b) Write short notes on the following: (10 marks)
Answer:
(i) RSA:
RSA (Rivest-Shamir-Adleman) is an asymmetric encryption algorithm used for secure data transmission. It relies on the mathematical properties of prime numbers to generate public and private keys.
Key Generation: RSA generates a pair of keys – a public key for encryption and a private key for decryption. The security of RSA is based on the computational difficulty of factoring large prime numbers.
Encryption and Decryption: Data encrypted with the public key can only be decrypted with the corresponding private key, ensuring confidentiality.
Applications: Widely used in secure communications, digital signatures, and key exchange protocols.
Advantages: High security due to the difficulty of factoring large numbers, widely supported in various security protocols.
Disadvantages: Slower performance compared to symmetric algorithms, large key sizes required for strong security.
(ii) OSI Model:
The OSI (Open Systems Interconnection) Model is a conceptual framework used to understand and implement network protocols in seven layers. Each layer has specific functions and communicates with adjacent layers.
Layer 1 - Physical: Deals with the physical connection between devices and the transmission of binary data over physical mediums.
Layer 2 - Data Link: Ensures error-free data transfer between two adjacent nodes, responsible for framing and MAC addressing.
Layer 3 - Network: Manages logical addressing and routing of data packets across the network.
Layer 4 - Transport: Provides end-to-end communication, error detection, and flow control, ensuring complete data transfer.
Layer 5 - Session: Manages sessions or connections between applications, handling setup, maintenance, and termination.
Layer 6 - Presentation: Translates data formats, encrypts/decrypts data, and compresses data for the application layer.
Layer 7 - Application: Provides network services directly to end-users and applications, such as HTTP, FTP, and email.
Advantages: Modular approach allows interoperability between different vendors' equipment, simplifies troubleshooting by isolating issues to specific layers.
Disadvantages: Overhead due to encapsulation/decapsulation processes, sometimes considered too theoretical and less practical compared to simpler models like TCP/IP.


